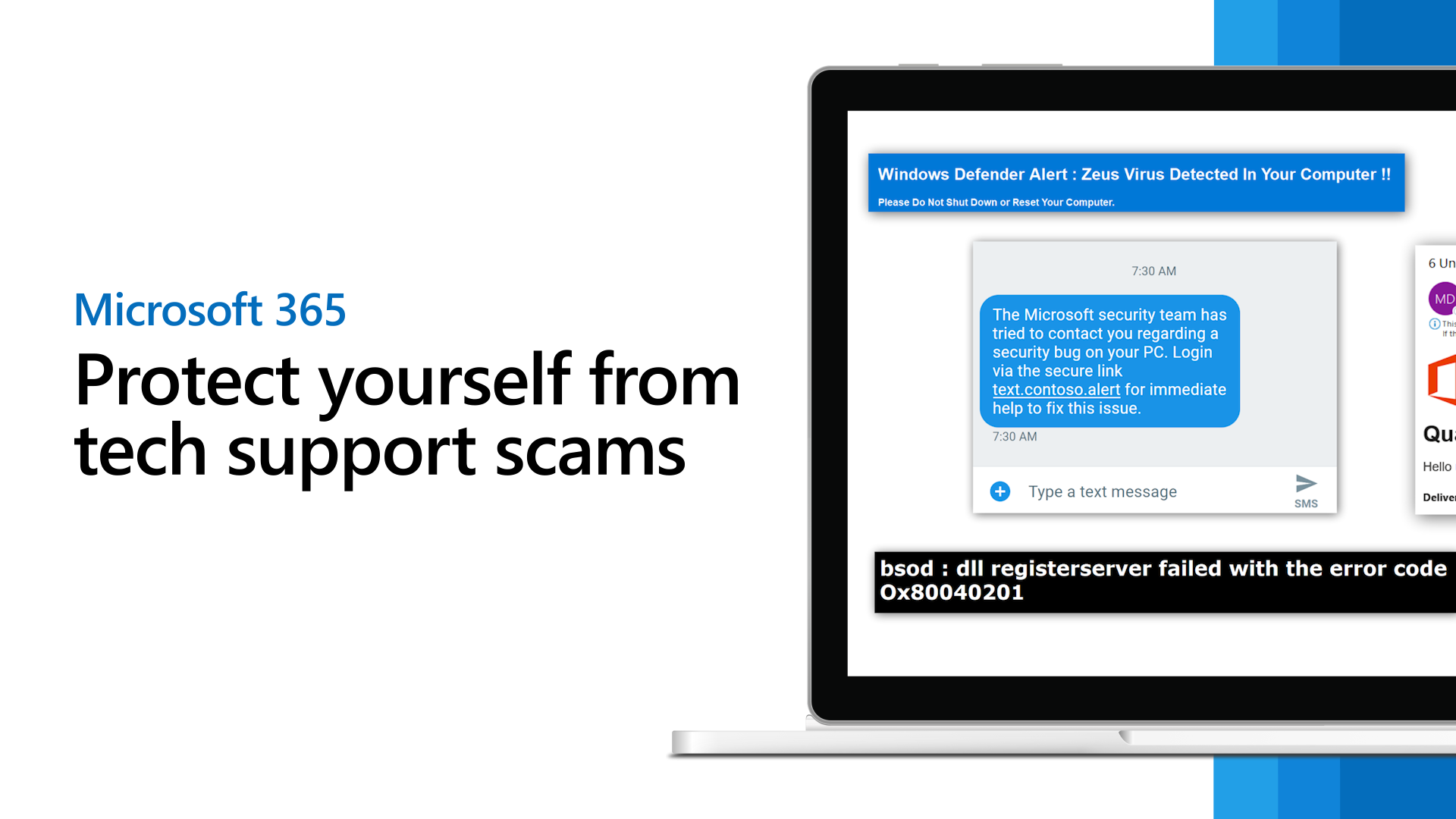
Premium Vector | Password phishing, hacker attack landing page template set. hackers steal personal data. internet security with tiny character insert password on website at huge pc. cartoon people vector illustration

13,600+ Phishing Illustrations, Royalty-Free Vector Graphics & Clip Art - iStock | Phishing email, Phishing icon, Email