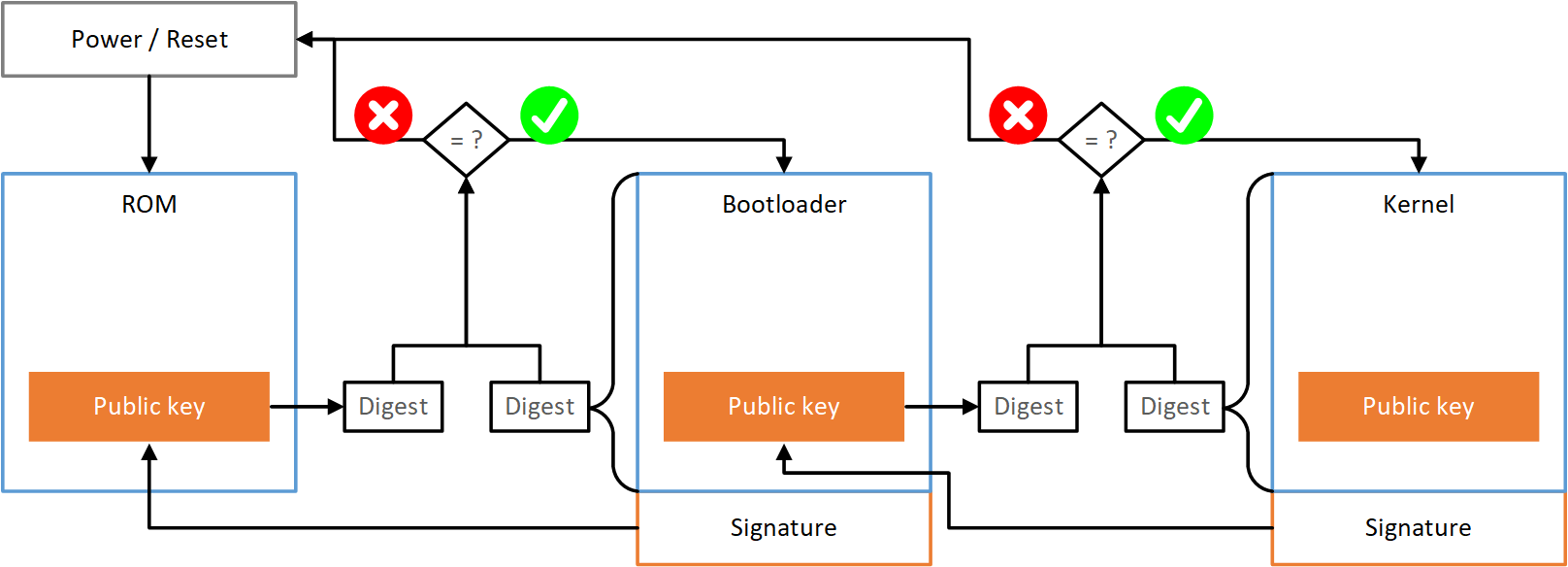
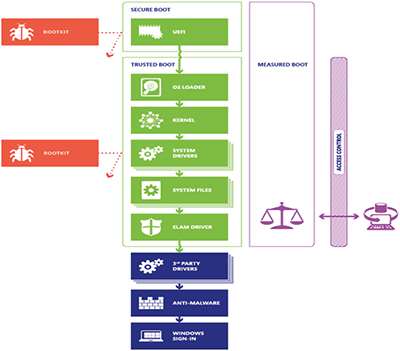
SOLVED: SECURE BOOT vs TRUSTED BOOT vs MEASURED BOOT, Whats the Difference? | Up & Running Technologies, Tech How To's

SOLVED: SECURE BOOT vs TRUSTED BOOT vs MEASURED BOOT, Whats the Difference? | Up & Running Technologies, Tech How To's
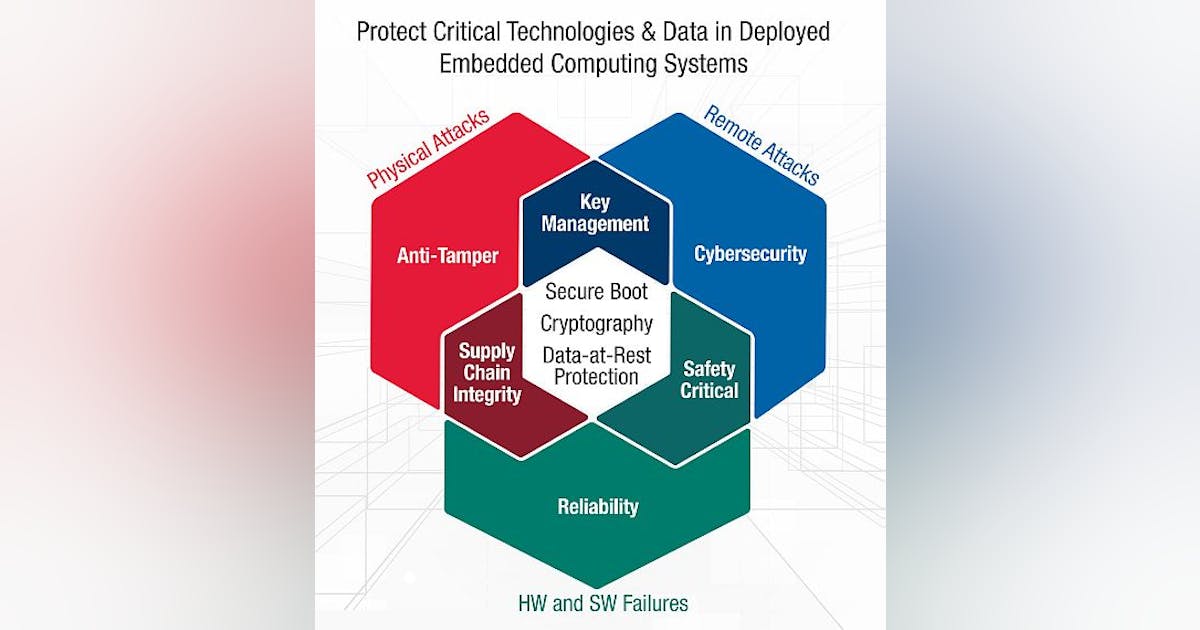
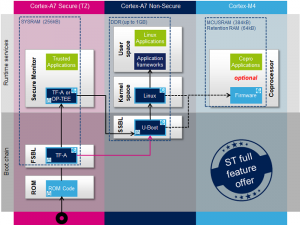
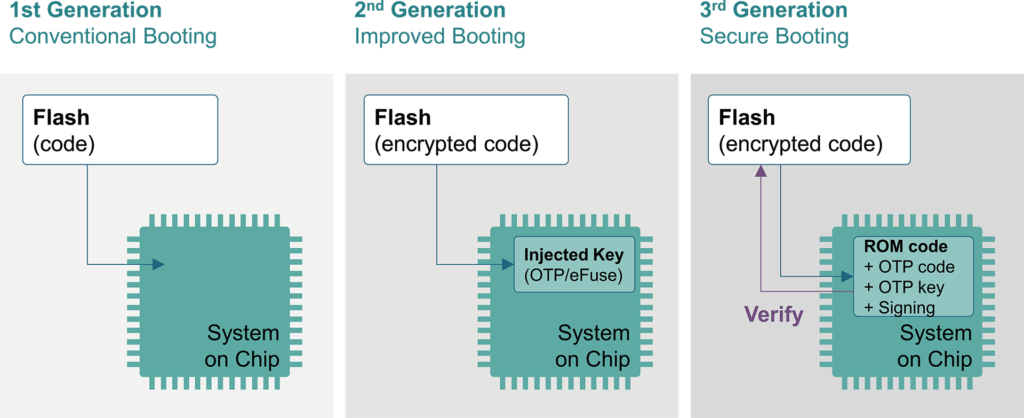
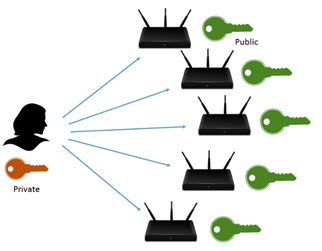
Trusted boot: a key strategy for ensuring the trustworthiness of an embedded computing system | Military Aerospace



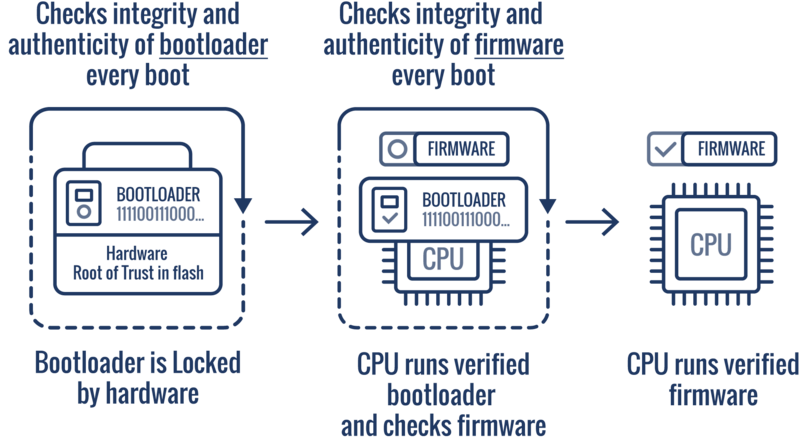




.png)